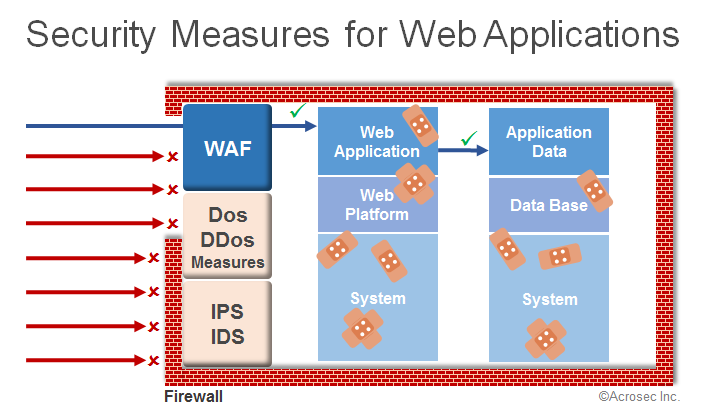
A WAF security solution is normally used for securing web applications in order to protect against attacks on the application layer. It filters requests that exploit application programming errors and application weaknesses or related vulnerabilities on the underlying application platform or system.
A WAF is typically deployed in front of web applications (network or service based solution). However, a WAF is just one important element in an orchestrated security setup. Following high level picture shows the main elements for securing external facing web applications:
A WAF is a great tool in order to secure web applications against existing and future threats. Virtual patching enables the application owner to handle upcoming security threats with more room to maneuver, allowing to fix security issues in applications not in panic mode but within the normal application development cycle.
A WAF can be far more than just a WAF
There is another good argument for having a WAF: A WAF can be an enabler for many enterprise application security scenarios at the boundary.
Looking at above picture, it is fairly obvious that a networked WAF (reverse-proxy) is the perfect place for value added services to applications. Unifying portal services, user authentication, access authorization, handling of security sessions, identity management, load balancing, high availability and failover scenarios are typical useful services to business, however, they are difficult to implement. Giving your developers a 500 page best practice security guide in order to develop these services is fine, but don’t expect that all applications will reach the same security level overnight.
Inbound WAF scenarios: Central secure web access server
The central web access server approach leverages a reverse proxy WAF as security gateway, creating a unique breed of framework that can be reused by all applications, reducing development cost, time to market and at the same time propping up the security level. This approach is known in the Swiss financial industry as “Swiss Style Web Entry Server” which is used to protect import applications, i.e. Internet banking.
Advantages:
|
Many firms with sensitive applications like Swiss banks combine such a central web access server with an appropriately designed DMZ network and identity management solutions. Such a design bundle is not only focused on security, but also on fostering reuse and integration. 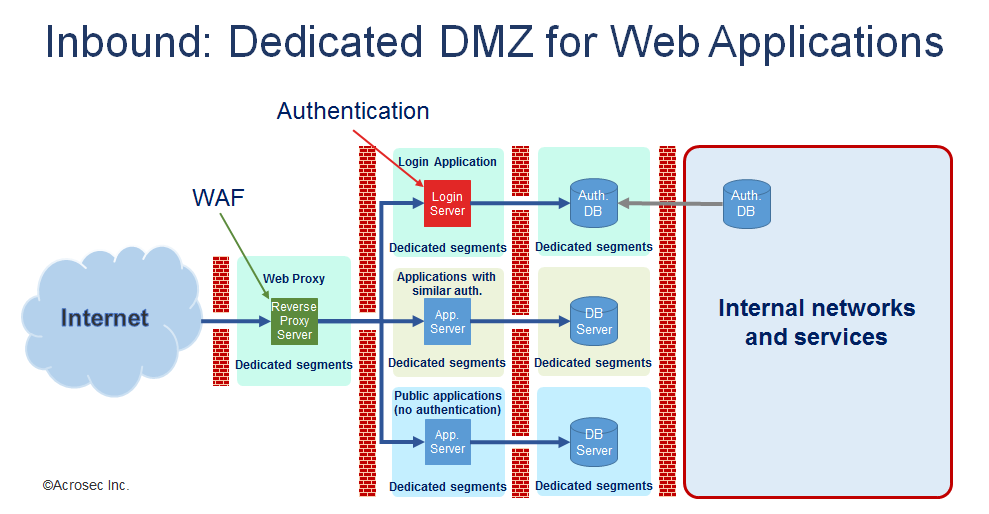
The scenario of having a central web access server is very flexible and supports a vast range of enterprise solutions, e.g. customer portals, Intranet remote access for employees or partner portals. Identity management and access control on URI resources is the key driver in order to enable such an approach.
Outbound WAF scenarios
Above scenarios are inbound focused (reverse proxy scenarios), however, a WAF can also be used for outbound scenarios. A WAF can be leveraged in outbound scenarios when it is acting as forward proxy. An outbound WAF specific filtering capabilities would be able to protect internal applications which consume external services, i.e. from business partners.
Examples:
- A WAF with dedicated SOAP/XML support can protect internal business applications when they use (connect to) external SOA based web services
- A WAF with adequate payload inspection can protect internal business applications when they use (connect to) external file transfer services on http protocol layer
Such scenarios seem unusual as forward proxies are rather known for securing the external browser traffic, e.g. preventing an employee to browse on malware infected web pages or preventing data leakage.
Examples of such outbound WAF solutions with SOAP/XML filtering capabilities have been implemented in the Swiss financial industry as security infrastructure for securely consuming external SOA web services from payment business partners (i.e. validator proxy solution).
Enterprise Security Architecture for realizing web application security
It is efficient to reuse what is difficult to implement by fostering standardization or to automate what is time consuming to do. It makes sense to reuse powerful security frameworks in order to combine cyber security with efficiency. However, this needs some decisions regarding who should do what on which layer.
The above WAF example is interesting for improving application security if it is also a secure reverse proxy which is versatile enough for covering many other security aspects in web application delivery. Leveraging such a secure reverse proxy as central entry point for all web applications has potential of strategic importance when it is to become part of an overall application layer cyber security concept.
Such an overall concept would be the realization of an Enterprise Security Architecture for all Internet facing web applications with many positive implications for business application strategy, IT Management and IT Governance. This example should make it clear that project based “Security by Design” requirements and Enterprise Security Architectures requirements are closely related.
Mandating the reuse of what is difficult to implement by individual developers and by making such standardized features centrally available improves not only cyber security, but it also increases overall cost efficiency of running web applications securely.
2016/02/05, last update 2018/07/04 ©ACROSEC Inc.